Integrating from Content Hub to enterprise systems - Security challenges
In a project where we're implementing Content Hub, there in a PIM system which is used to manage products that feed into various downstream systems.
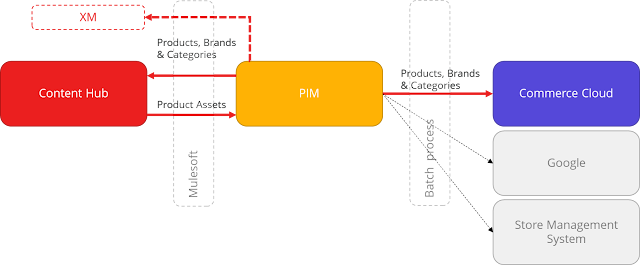
Content Hub is to be the new source of truth for Digital Assets, and this will include all product images. We already have various entities mastered in other systems including PIM such as products and categories bing syncrhonised into Content Hub as taxonomies that will enable tagging of Digital Assets to assist in organising them. This integration is done via Mulesoft with the PIM system raising an event when an individual product/category is changed, with a Mulesfot subscriber responding to the event and pushing the change to Content Hub via it's REST interface.
In our case we want the association of product images with products in Content Hub to control what images are shown for products in downsteram systems. This means that data will flow from Content Hub back through Mulesoft and into PIM. PIM then manages the flow of the information to downstream systems such as the e-Commerce platform and Store Management system
The complication
Being an enterprise environment, there are existing standards and patterns for external systems (which Content Hub is, being an externally hosted SaaS platform). The two key requirements for calling into the client Mulesoft environment APIs, which will themselves then update core internal systems, are:
- Calls to APIs must be authenticated/authorised using OAuth tokens issues from AWS Cognito
- Call to APIs must come from IP whitelisted source systems
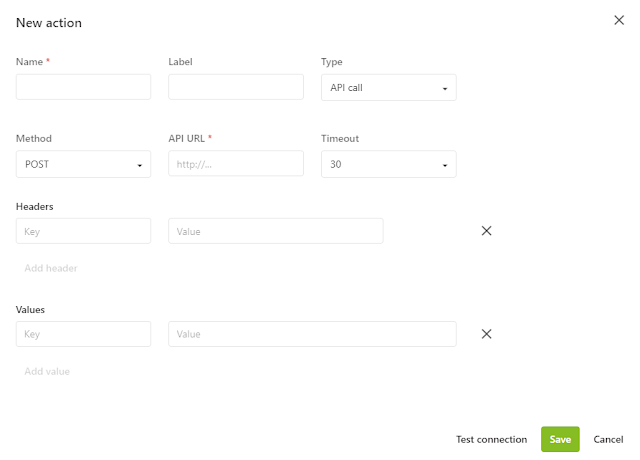
If we were able to implement even one of these two requirements that might have been acceptable, however Content Hub makes both of these difficult. Even using dedicated SKUs of the product such as Corporate/Enterprise, there isn't the ability to have a static source IP address. Sitecore support was able to advise us of source IPs per environment, however these are not guarenteed not to change. Furthermore, whilst the API trigger allows you to specifiy headers which are sent with the request, there is no inbuilt capability to perform an OAuth authentication - and Content Hub doesn't allow direct API calls from code
Compensating controls
The major risks for the client of allowing the calls from external systems that could:
- Make unauthenticated calls to the systems;
- Compromise internal systems through embedding of spurious information (e.g. code injection issues); or
- Compromose the client website by pushing data (such as image URLs) that is incorrect and damaging to the brand (i.e. defacing the site)
As we couldn't leverage the standard pre-approved integration patterns, we instead looked for optoins to provide compensating controls addressing those risks.
- To address code injection risks, we decided to ensure that all payloads were routed through the CloudFront WAF. This will allow policy to be applied to help detect and stop any requests that attempt code injection (amongst other secuerity risks).
- As direct connectivity to Mulesoft using OAuth isn't possible, connect to a custom API exposed through AWS API Gateway which allows API Keys to be applied as policy. This still requires that the API key value be configured into Content Hub API action on a per environment basis - this isn't perfect, and will need to be rotated manually for proper security.
- The request will be routed to a custom proxy API which we will host in the container platform similarly to any other external facing APIs such as BFF APIs. This proxy API will:
- Authenticate to Mulesoft via OAuth using AWS Cognito as per authorised patterns
- As it lives within the client internal environment already, doesn't need to be IP whitelisted
- Apply some additional validation checks, in this case ensuring any image URLs provided in the baseline point to assets in the client's Content Hub domain
The ability to support the OAuth client credentials flow for API actions would be a great addition to Content Hub, I hope it's something we get in future. In the meantime, integrating to enterprise systems with enterprise security policies applied may mean some additional steps and lateral thinking.


Comments
Post a Comment