Cloud hosting Sitecore - Disaster Recovery
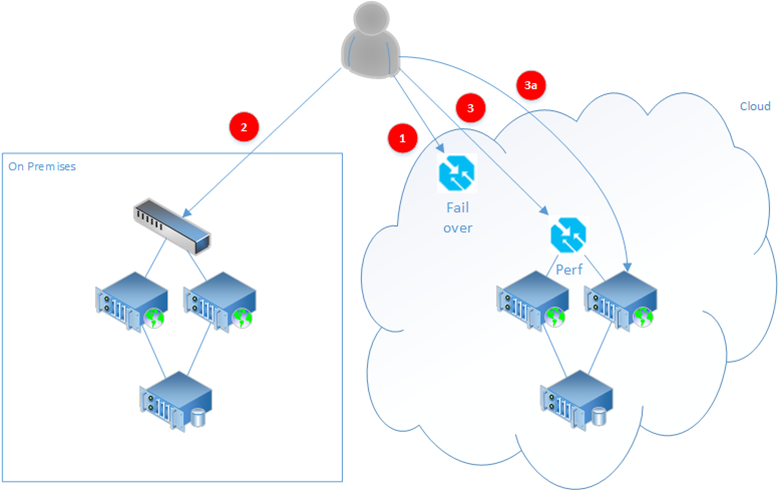
In my previous posts in this series, I looked at how you can use the global reach and deployment automation capabilities of the cloud to provide Sitecore installations that support users located at various points around the globe without compromising on the analytics and personalisation capabilities of the Sitecore platform. In this post I look at how you can use the benefits of the cloud to provide automated DR failover for your existing on-premise hosted website. Other posts in this series Cloud hosting Sitecore - High Availability Cloud hosting Sitecore - Scaling for peak loads Cloud hosting Sitecore - Serving global audiences Cloud hosting Sitecore - Cloud development patterns Pattern 4: Disaster Recovery Sometimes you don't need to have Sitecore running actively at multiple locations, and perhaps you are already providing hosting on premises and only want to use the cloud to provide a standby service in the event of an outage of the primary hosting environment.



